In the field of cybersecurity and data protection, two fundamental techniques—encryption and hashing—are widely used to secure information. Both processes convert readable data into a different, often unreadable format, but they do so for entirely different reasons and through very different mechanisms.
Understanding how encryption and hashing differ is essential for designing secure systems, managing sensitive data, and ensuring the confidentiality, integrity, and authenticity of digital communications. This article explores both concepts in detail, outlines their key characteristics, and highlights practical use cases for each.
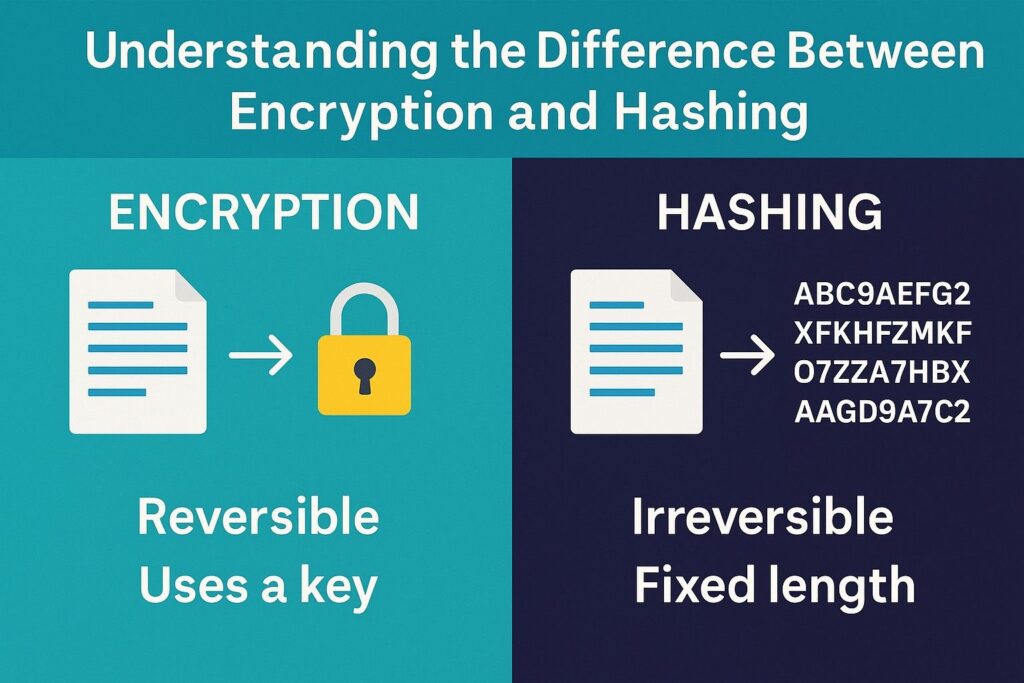
What Is Encryption?
Encryption is the process of transforming plaintext (readable data) into ciphertext (unreadable data) using a mathematical algorithm and a cryptographic key. The primary goal of encryption is confidentiality, meaning only authorized parties with the correct key can convert the ciphertext back into its original form through a process called decryption.
Encryption is reversible, and this reversibility is what makes it suitable for data transmission, storage, and retrieval in secure systems.
Key Concepts in Encryption:
- Plaintext: The original, human-readable data, such as a message, file, or password.
- Ciphertext: The encrypted, scrambled version of the plaintext.
- Key: A secret value used by the encryption algorithm to transform data. Without the correct key, decrypting the data is computationally infeasible.
- Algorithm: A formal set of rules used for encrypting and decrypting data.
Types of Encryption:
1. Symmetric Encryption
- Uses a single secret key for both encryption and decryption.
- Faster and more efficient, especially for large data sets.
- The key must be securely shared between parties.
- Common algorithms: AES (Advanced Encryption Standard), DES (Data Encryption Standard), RC4
2. Asymmetric Encryption
- Uses a pair of keys: a public key (for encryption) and a private key (for decryption).
- More secure for transmitting data over untrusted networks.
- Common algorithms: RSA (Rivest–Shamir–Adleman), ECC (Elliptic Curve Cryptography)
Real-World Use Case for Encryption:
- HTTPS (HyperText Transfer Protocol Secure) encrypts all data exchanged between a user’s browser and a website’s server, protecting sensitive information such as login credentials, payment data, and personal details from eavesdropping.
What Is Hashing?
Hashing is a process that takes an input (or message) and returns a fixed-length string, which is typically a representation of the input known as a hash value, digest, or checksum. Hashing is deterministic (the same input always gives the same output) and non-reversible—it is practically impossible to derive the original input from the hash value.
The primary goal of hashing is data integrity and authentication, rather than confidentiality. Hashing helps detect whether data has been altered.
Key Characteristics of Hashing:
- One-Way Function: Once data is hashed, it cannot be reverted to its original form.
- Fixed Output Length: Regardless of input size, the output hash is of constant length (e.g., 256 bits for SHA-256).
- Deterministic: Same input always results in the same hash.
- Collision-Resistant: It is difficult to find two distinct inputs that produce the same hash.
Popular Hashing Algorithms:
- MD5 (Message Digest 5): Fast but insecure due to known vulnerabilities.
- SHA-1 (Secure Hash Algorithm 1): More secure than MD5, but now considered weak.
- SHA-2 (includes SHA-256 and SHA-512): Currently recommended for secure hashing.
- SHA-3: The latest standardized hash function designed to resist known attacks.
Real-World Use Case for Hashing:
- Password Storage: When a user creates an account, their password is hashed and stored in the database. During login, the entered password is hashed and compared with the stored hash. This way, even if the database is compromised, the actual passwords remain protected.
Key Differences Between Encryption and Hashing
| Feature | Encryption | Hashing |
|---|---|---|
| Purpose | Ensures confidentiality of data | Ensures data integrity and authenticity |
| Reversibility | Reversible with the appropriate decryption key | Irreversible (one-way function) |
| Output Size | Varies depending on input and algorithm used | Always produces a fixed-length output |
| Input Type | Plaintext (files, messages, media) | Any input data (text, file, password, etc.) |
| Output Format | Ciphertext (non-readable and encrypted) | Hash value or digest (fixed-length string) |
| Security Mechanism | Uses keys (symmetric or asymmetric) | Uses mathematical functions without keys |
| Primary Use Cases | Data encryption during communication and storage | Verifying data integrity, password authentication |
| Vulnerabilities | Brute force attacks, key leaks, implementation flaws | Hash collisions, outdated algorithms (e.g., MD5, SHA-1) |
When to Use Encryption vs. Hashing
Understanding when to use encryption versus hashing is crucial for implementing proper security protocols:
Use Encryption When:
- You need to protect sensitive data that may need to be accessed or read later.
- Secure email communications, database records, or files during transit or storage.
- You require confidentiality in client-server interactions or messaging platforms.
- You want to implement secure end-to-end encryption between two parties.
Use Hashing When:
- You need to verify that data has not been altered during transmission or storage.
- Storing user passwords securely in a database.
- Creating digital signatures or data fingerprints for document verification.
- Performing data integrity checks (e.g., checking whether a downloaded file is corrupted).
Can Encryption and Hashing Work Together?
Yes, in many security architectures, encryption and hashing are used together to provide both confidentiality and integrity. A typical example is digital signatures, which combine both techniques as follows:
- A message is hashed to produce a digest.
- The digest is encrypted with the sender’s private key to form the digital signature.
- The receiver decrypts the signature using the sender’s public key and hashes the received message.
- The two hash values are compared to verify the message’s authenticity and integrity.
This approach is widely used in blockchains, SSL certificates, and secure email protocols like PGP.
Common Pitfalls and Security Recommendations
- Never use encryption alone for password storage. Always use hashing with a salt to prevent rainbow table attacks.
- Avoid using deprecated algorithms like MD5 and SHA-1. Use SHA-256 or SHA-3 for modern security needs.
- Secure your encryption keys using key management systems. Exposure of keys can compromise the entire security of encrypted data.
- For secure hashing in passwords, use adaptive functions like bcrypt, scrypt, or Argon2, which introduce computation time to deter brute-force attacks.
Final Thoughts
Encryption and hashing are both critical tools in the cybersecurity toolbox, but they serve distinct purposes. Encryption is primarily about protecting the confidentiality of data, while hashing is focused on ensuring data has not been tampered with.
Selecting the correct technique depends on your specific use case. If you need to read the original data later, use encryption. If you only need to verify the integrity or compare data without revealing the original, use hashing.
Understanding the difference—and how to combine both effectively—is essential for developing secure applications, protecting user data, and building trust in digital systems.

I’m Shreyash Mhashilkar, an IT professional who loves building user-friendly, scalable digital solutions. Outside of coding, I enjoy researching new places, learning about different cultures, and exploring how technology shapes the way we live and travel. I share my experiences and discoveries to help others explore new places, cultures, and ideas with curiosity and enthusiasm.